OWASP Top 10

OWASP's "Ten Most Critical Web Application Security Risks"
Threat Modelling
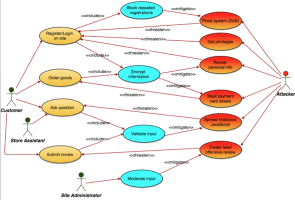
Security requirements analysis using misuse cases
Security Assignment

This assignment requires you to prepare a report based mainly on your practical experience with web application security.
Lab-17 Misuse Cases
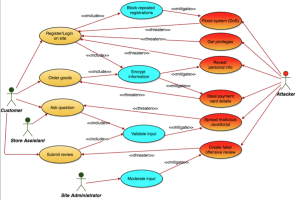
The focus of this lab is this first part of the security assignment, which is broken down into the following steps: